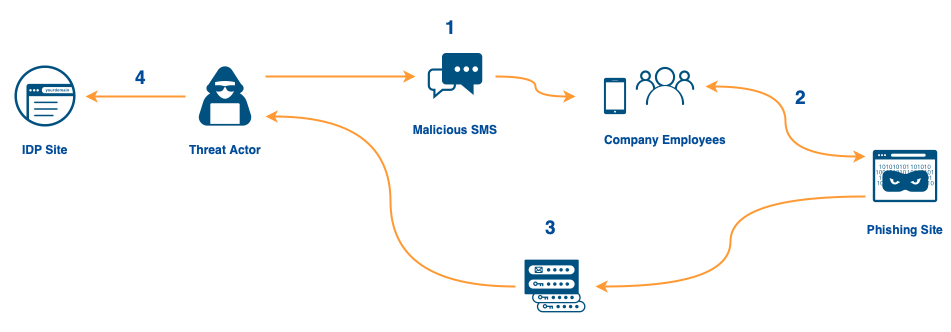
Let’s review attacks of the last weeks (well, months …) against users of a well-known IDaaS platform using tailored SMS Phishing vectors. The described attack and threat patterns have been described as Scatter Swine by Okta and 0ktapus by others. The performed attack provides a great learning experience on Supply Chain Attacks and shows the great risk companies are facing with outsourcing their identity management.
Okta is the main target we’re looking at as an identity-as-a-service (IDaaS) provider. Okta provides a platform enabling employees to use a single login to access all software assets within a company. We will review the Twilio attack, which enabled a Threat Actor to attack Okta via weak Multi Factor Authentication (MFA) options. In addition, these breaches also led to supply-chain attacks on customers using these services, such as Signal and DigitalOcean. Furthermore, we are looking into the same style of attack performed against Cloudflare and how they managed to mitigate it.
We will also correlate available data, provide a timeline of events and of course highlight mitigation and prevention mechanism.
Cloudflare
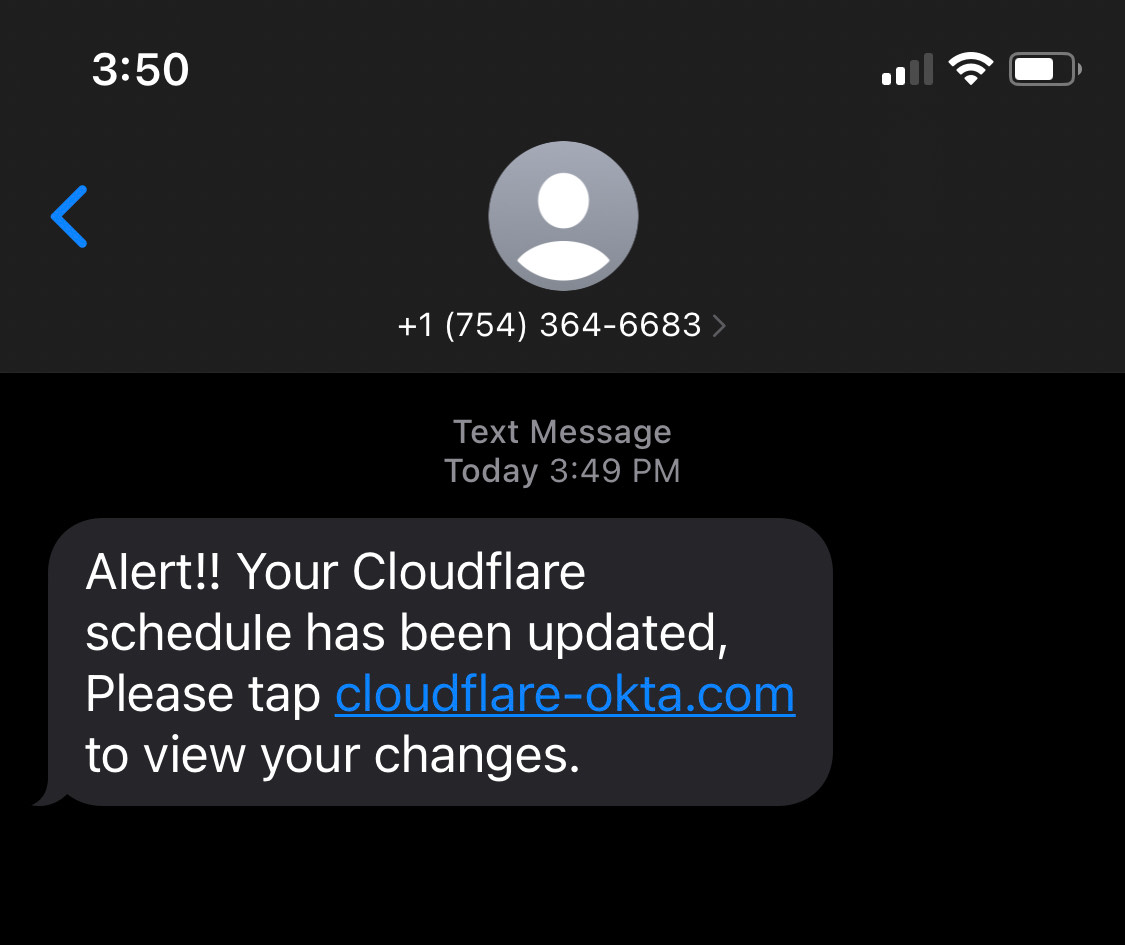
Cloudflare is a content delivery network and DDoS mitigation provider. On the 20th of July 2022 Cloudflare were attacked via targeted text messages:
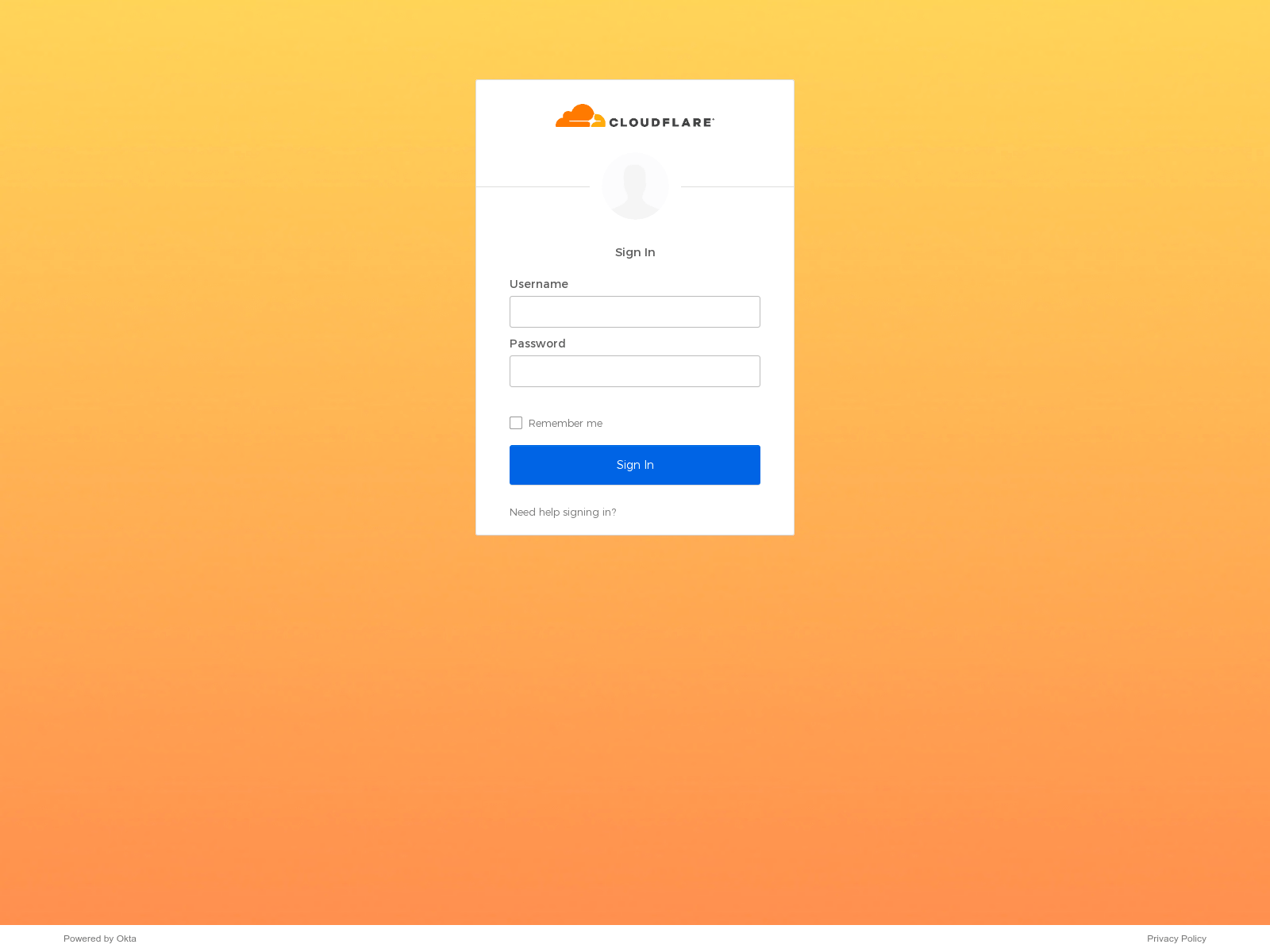
The phishing page returned a legitimate looking Okta login page, just as Cloudflare would use it in production:
When credentials are entered, the attacker’s backend would relay the Time-based One-time Password (TOTP) code before it expires via Telegram to enable a real-time phishing attack:
Cloudlfare mitigated the attack by using FIDO2 security keys and by rolling out a playbook for responding to targeted phishing attacks.
Twilio
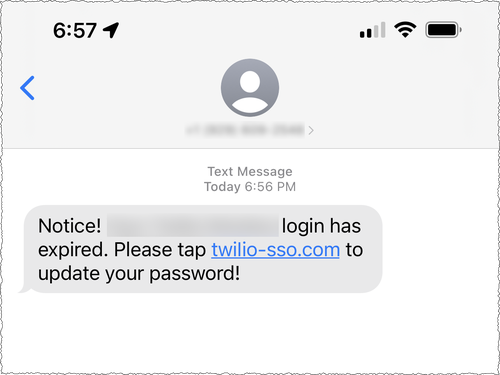
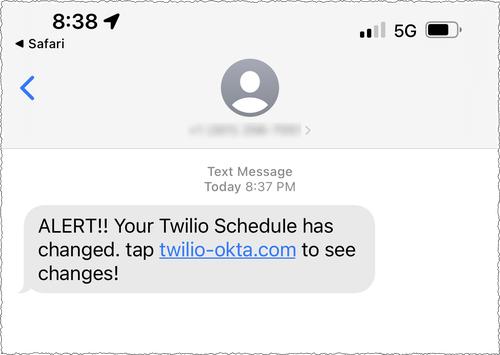
Twilio is a Customer Engagement Platform which provides programmable communication tools. On the 4th of August 2022 Twilio became aware of a targeted phishing text message circulating on their employees’ mobiles:
The Twilio team has seen different URLs that were using words including „Twilio,“ „Okta,“ and „SSO“ to try and trick users to click on a link. Once clicked the link would take the user to a landing page that impersonated Twilio’s sign-in page.
The threat actor was able to harvest employee credentials from Twilio. The attackers then used the stolen credentials to gain access to internal systems where they were able to access customer data.
As of 24th of August about 163 Twilio customers and 93 Authy users’ data has been accessed.
OKTA
Okta provides its customers with multiple forms of authentication for services, including temporary codes delivered over SMS through Twilio. On the 8th of August 2022, Okta learned that the Twilio hack exposed relevant authentication data for a specific Okta client. The attacker searched for 38 phone numbers which are almost all linked to a single organisation.
Timeline
Summary
The attackers OSINT clearly failed on missing the important bit that Cloudflare uses FIDO2 security keys internally. It is surprising that the attacker managed to gather the mobile phone numbers from internal employees and family members, but then missing that their phishing attempts would render unsuccessful because of it..
With our Attack Simulation service you can proof that your multi factor authentication solution is resilient against sophisticated phishing attacks. Additionally, you can train your IT department and validate your playbooks. This attack once more shows that, Phishing exercises are still a thing in 2022. However, the focus has (thankfully) just shifted from pure E-mail-based phishing to alternate delivery methods.
Lesson learned
Lesson learned, don’t use SMS based 2FA/MFA – and no, it is not alright for Backup purposes either.

Cloudflare did the right thing by enforcing FIDO2.0 Security Keys and following up the attack according to a playbook. When you want to secure your users against Phishing we recommend:
- Implement FIDO2 hardware tokens
- Implement and promote reporting channels for user to report attacks
- Have a playbook ready to follow up and investigate the reported phishing attacks
- Train your users; Train your IT team and Train your Software and Hardware solutions; Don’t allow weak fallback options.
- Simulate attacks to validate the correct implementation of your strategy
In general, perform more attack simulations in creative ways to build more awareness for social engineering attacks that are not the norm (or just fitting perfectly in how you’re operating). Social Engineering awareness should always be more than just E-Mail Phishing and it is a great way to expand your IT department playbook on following up with successful phishing engagements too.
For example, you could implement different factors in your phishing awareness training, like using Voice, SMS/WhatsApp/Signal messages or less common routes like Microsoft Teams or Slack. We have helped clients implementing tailored and sophisticated attack scenarios using Voice Messages and chained vectors like letters and virtual USB keyboards (Rubber Ducky) too.
Want to learn more about how we’re performing breach simulations via phishing in different ponds than just E-Mail?
References
- [1] Why You Should Ditch SMS as an Auth Factor
- [2] Detecting Scatter Swine: Insights into a relentless phishing campaign
- [3] 0ktapus campaign: Twilio, Cloudflare, and over 130 more victims discovered by Group-IB
- [4] Twilio hackers hit over 130 orgs in massive Okta phishing attack
- [5] Okta one-time MFA passcodes exposed in Twilio cyberattack
- [6] Incident Report: Employee and Customer Account Compromise
- [7] The mechanics of a sophisticated phishing scam and how we stopped it
- [8] Roasting 0ktapus: The phishing campaign going after Okta identity credentials
Author

Sven Schlüter
sven@y-security.de
Y-Security GmbH
02. September 2022