
This spring we at Y-Security challenged ourselves by completing both Red Team focused certifications Red Team Ops I & II offered by Zero-Point Security.
While they also offer a few other courses more focused on development of offensive tools, these two courses are their biggest and most popular courses.
Red Team Ops I
Red Team Ops is an online, self-study course that teaches the basic principles, tools and techniques synonymous with red teaming.
Students will first cover the core concepts of adversary simulation, command & control, engagement planning and reporting.
They will then go through each stage of the attack lifecycle – from initial compromise to full domain takeover, data hunting and exfiltration. Students will learn how common „OPSEC failures“ can lead to detection by defenders, and how to carry out those attacks in a stealthier way.
Finally, they will learn how to bypass defences such as Windows Defender, AMSI and AppLocker.
Zero-Point Security
Red Team Ops II
Learn how to build secure and resilient on-premise C2 infrastructure, using public cloud redirectors and HTTPS.
Go deeper into C++ and C# programming with Windows APIs, leading into writing custom tooling for a variety of offensive actions including process injection, PPID spoofing, and command line spoofing.
Learn how to clean up memory indicators of Cobalt Strike’s Beacon, and leverage in-memory obfuscation to bypass some memory scanning techniques.
Employ strategies for enumerating, identifying, and exploiting weaknesses in Attack Surface Reduction and Windows Defender Application Control technologies.
Bypass AV and EDR agents by circumventing ETW, userland hooking, and kernel callbacks.
Zero-Point Security
Course Material & Preparation
Both courses offer written material separated by chapters, that can be checked off once completed. The Red Team Ops I course also offers video modules on some chapters, which are helpful when following along with certain practice steps.
The first course (Red Team Ops I) focuses on variety of Active Directory focused attacks and techniques and how to perform them. As the main tool for Command and Control both courses use Cobalt Strike. Even though I already completed the similar OSEP certification, there were a few key differences where the Red Team Ops courses stand out. For example it also teaches how to detect each of the shown attacks and their OPSEC relevance and what to keep in mind when performing real Red Team engagements. I really liked this aspect about the courses.
The second course (Red Team Ops II) is a continuation of Read Team Ops I. It focuses heavily on customizing and improving your TTPs to be stealthy and go undetected against enterprise grade EDRs. When you decide to tackle this course and the exam, be prepared to write a lot of C# and C code. You will have to become familiar with the Windows API and internal windows mechanisms.
Completing the Red Team Ops 1 course is highly recommended, unless you are already familiar with Cobalt Strike and Active Directory attacks.
Practice with the Labs
The accompanying Labs for the courses are provided through Cyber Ranges Snap Labs, which is part of Immersive Labs. Unlike other training providers, SnapLabs doesn’t give you the ability to use your own virtual machines in the lab. This means there is no VPN connection available. Instead, the lab is powered by Apache Guacamole, which is a web interface for remote connections, such as Remote Desktop or VNC. While you might have to deal with performance issues, you are guaranteed a working system with all required tools pre-installed. This includes an active Cobalt Strike license, so you don’t need one yourself.
The lab offers an entire AD with all special systems and attack vectors that are shown in the course. It’s worth mentioning that the lab is not in a classic CTF style. It’s more like a playground where you can access each machine and thoroughly practice and analyze your attacks and tools. This is especially helpful when you are testing your payloads against AV & EDR products.
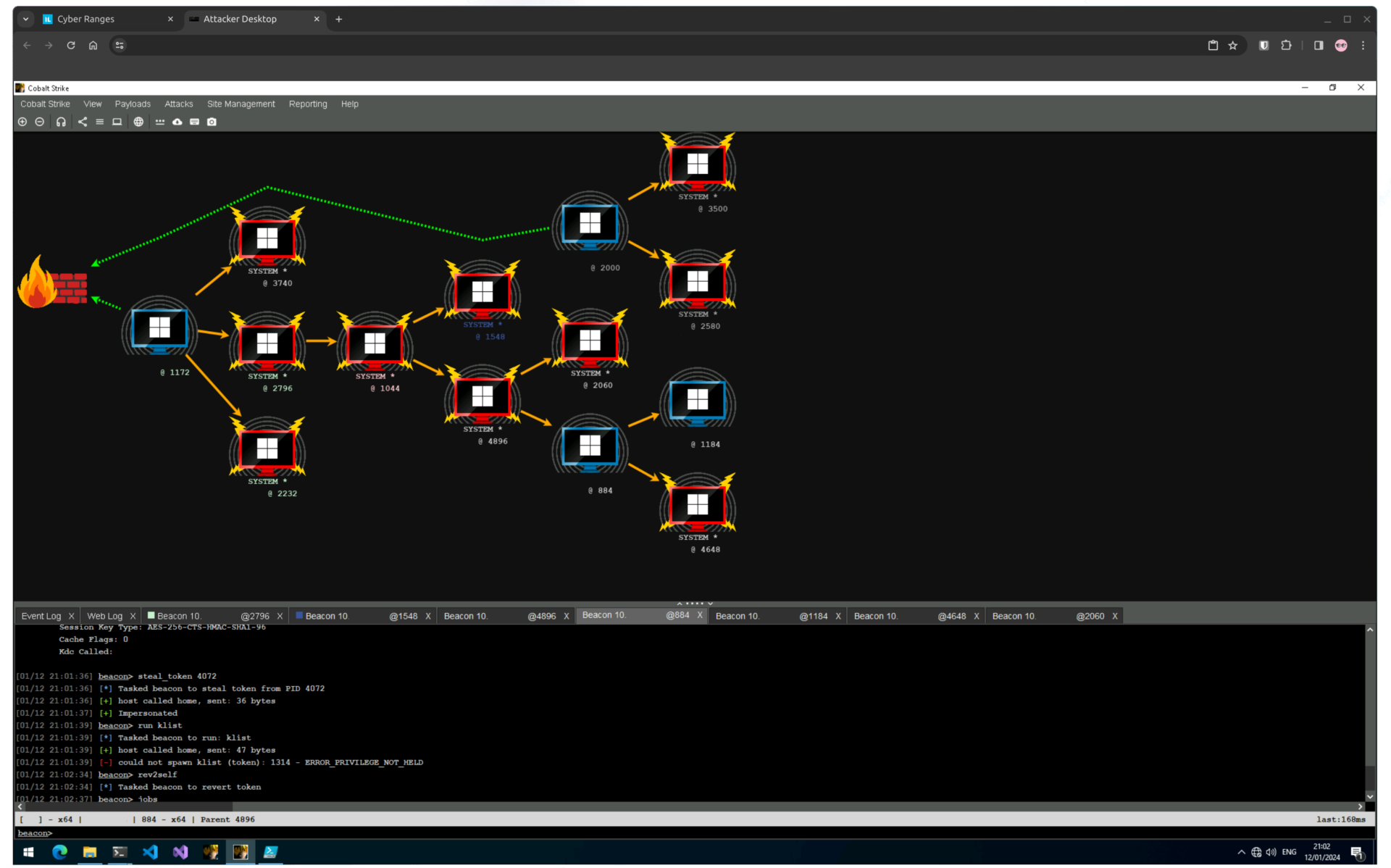
Exam
I won’t spoil any of the content here, but instead I would like to share my personal experience from both exams. First of all, the time constraints of 72 & 96 hours seem very daunting, but realistically you shouldn’t need all this time. It’s more so to give yourself flexibility and take the time crunch away that many other exams can have.
Red Team Ops I

My biggest preparation for the RTO I exam was ensuring that I had a working shellcode runner which wouldn’t get flagged and removed by Windows Defender, as it is also suggested in the course material.
During the exam I felt that I always knew what steps I had to take and what to do next. For me the challenging part of the exam was more about preparation of tools and evading AV than figuring out the attack path.
My advice is to work methodically, think about the logic and have the course material open next to you. There isn’t anything new or out of the ordinary in the exam, which hasn’t been discussed in the material. I finished the exam after roughly 10 hours and spent some additional time to get the remaining flags, purely because I enjoyed the exam and had so much time left anyway.
It can probably be done in less time, but the 72 available hours are extremely generous. Time shouldn’t be a worry at all.
Red Team Ops II
While the first exam was more easy going for me, the RTO II exam was totally different. It proved to be a real challenge for me and I had to prepare my payloads extensively, which I also had to slightly adapt during the exam, in order to be undetected by the EDR used in the course.
The exam is a slightly smaller version of the RTO I exam but with a much better defence and EDR in place.

Similar to the other exam, I felt like I had a good plan for the attack path, but since I didn’t spend much time in the labs compared to RTO I, I had to spend a significant amount of time adapting my toolkit during the exam.
In the lab environment you can simply login to your target machine and check the logs to see what went wrong. This is rather difficult in the exam because you are still trying to get access to your target and cannot identify if an attack was detected or not – except that no beacon popped up in the console.
If you feel ready to tackle your exam, make sure your toolkit works and you have an established method to test them against EDRs and AVs.
My advice here is to test as many scenarios and attacks as possible beforehand and make sure your tools work correctly and aren’t flagged in different situations. Because of the time I spent adapting tools and payloads during my exam, I probably took a lot longer than I actually needed.
After a few days however I managed to find a good „flow“ that worked for me and finished the exam shortly after. Overall, I spent roughly 30-35 hours actively working on the exam, which includes adjusting my payloads and tools.
Conclusion
Christian Becker

The Red Team Ops courses give a good overview about commonly used attack and defense evasion techniques used in adversary simulation assessments.
Christian Becker
The scenario in the exam is based upon realistic vulnerabilities that we also encounter during our Red Team exercises.
While I enjoyed the time flexibility of the exam I also need to admit that the provided attacker machines could have more resources available as the system was very slow and unresponsive during tool compilation and general usage.
Thore Imhof

Both courses were really enjoyable and offer a lot of value for it’s relatively low price-point. I like that they are both focused on real world examples and also show the other side of the coin, meaning the defenders and how they go about to detect us red teamers.
Thore Imhof
This helped me gain a better understanding about opsec during an operation and what to do or whatnot to do.
It’s definitely a recommendation from me and I’m keen to also check out Zero Points more development related courses!

Thore Imhof
thore@y-security.de
Y-Security GmbH
16. April 2024
